Malware analysis is available for free with SafeDep Cloud. See pricing for more details
Supported Ecosystems
npm
JavaScript and TypeScript packages
PyPI
Python packages and wheels
Go Modules
Go language modules
RubyGems
Ruby packages and gems
GitHub Actions
GitHub Action workflows
VS Code Extensions
Visual Studio Code extensions
Requirements
Install vet
You must have vet version
1.9.7 or above installedSafeDep Cloud Access
You must be onboarded to SafeDep Cloud with:
- Tenant Domain
- API Key
Repository Scanning
Basic Malware Scanning
Enable malware analysis with the--malware flag:
We make a trade-off between coverage and speed.
vet waits for a timeout period for malware analysis to complete. This works well for pull requests and CI/CD pipelines where the number of changed packages is usually low.Timeout Configuration
Adjust analysis timeout for different scenarios:Specific Manifest Scanning
Scan individual package manifest files:PURL-Based Scanning
Scan specific packages using Package URLs: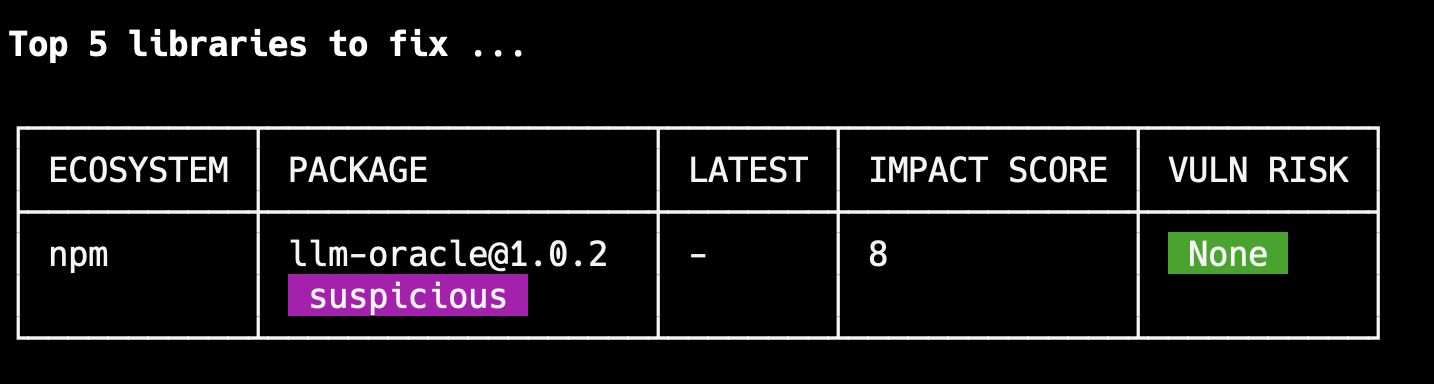
Visual Studio Code Extensions
Scan locally installed VS Code extensions:GitHub Actions Integration
vet-action Cloud Mode
Enable malicious package protection in GitHub repositories using vet-action:Pull Request Integration
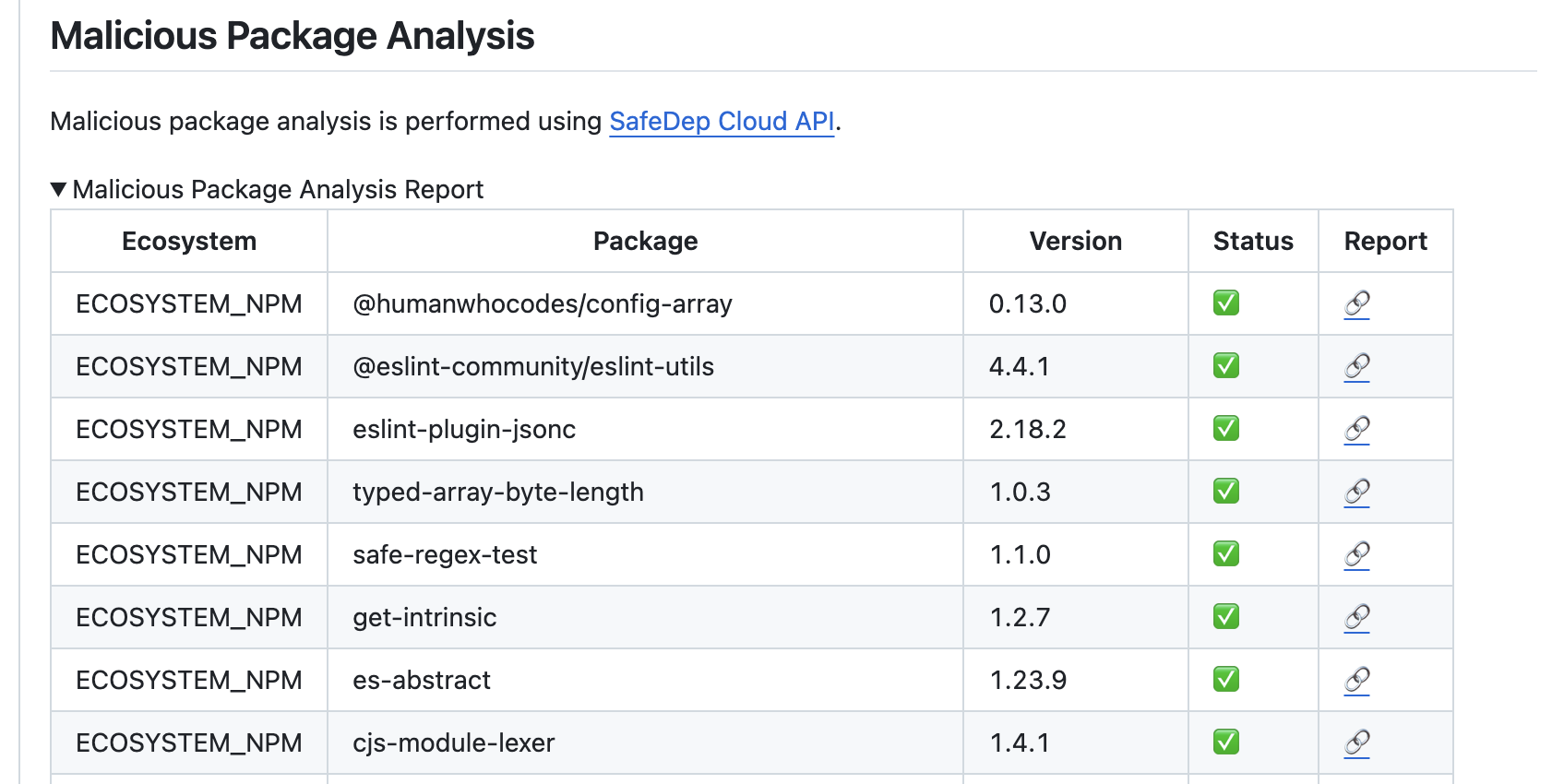
When enabled, vet scans changed packages for malware and provides results directly in pull requests: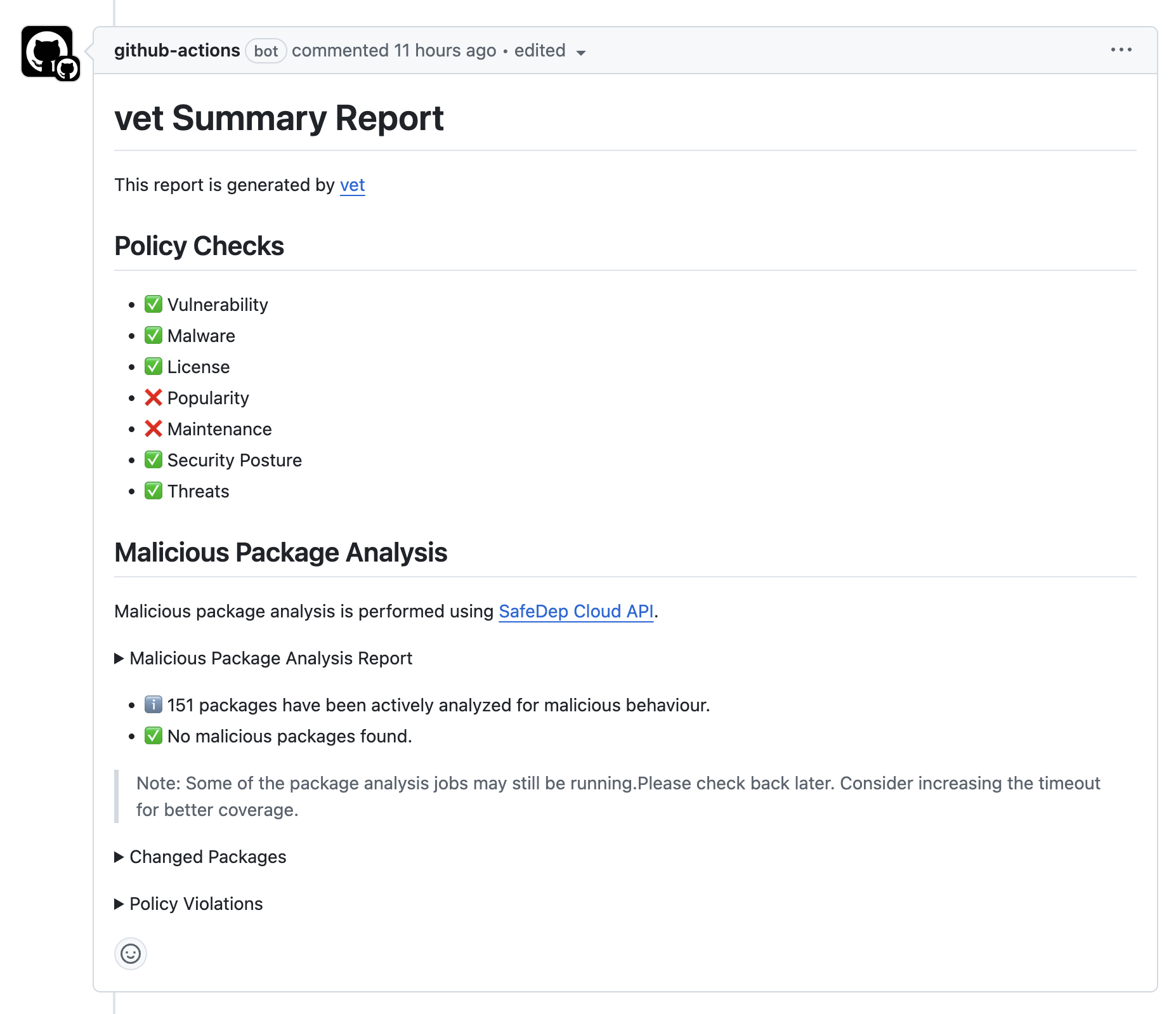
Package Inspection
Enable Experimental Feature
Package inspection is currently experimental. Enable it with:Inspect Single Packages
Perform detailed analysis of individual packages:Package analysis is performed asynchronously. Scanning usually takes a few minutes but may take longer depending on the analysis queue.
Analysis Results
On completion, vet shows the analysis status and classification: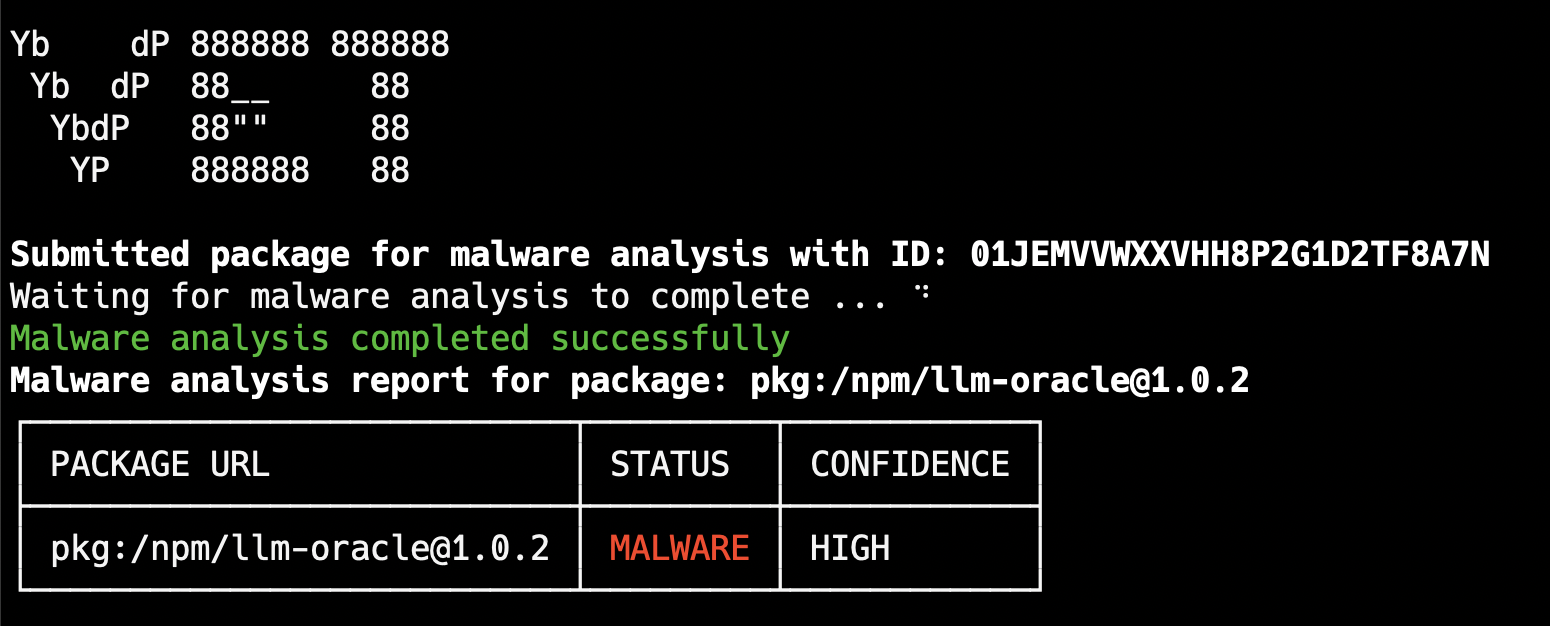
Export Results
Export analysis results as JSON:Understanding Results
Classification Levels
- SAFE: No malicious behavior detected
- SUSPICIOUS: Potentially risky patterns identified
- MALICIOUS: Confirmed malicious behavior found
Analysis Techniques
Static Analysis
Static Analysis
- Code pattern analysis
- Suspicious function detection
- Obfuscation identification
Behavioral Analysis
Behavioral Analysis
- Network communication patterns
- File system access patterns
- Process execution analysis
Metadata Analysis
Metadata Analysis
- Package metadata anomalies
- Publisher reputation analysis
- Distribution pattern analysis
CI/CD Integration Examples
GitLab CI
Jenkins Pipeline
Best Practices
Performance Optimization
Performance Optimization
- Use shorter timeouts for CI/CD environments
- Scan only changed packages in pull requests
- Cache analysis results when possible
Security Integration
Security Integration
- Fail builds on malicious package detection
- Set up alerts for suspicious packages
- Regularly scan entire dependency trees
Team Workflow
Team Workflow
- Train teams on interpreting results
- Establish response procedures for malicious findings
- Document approved exceptions for false positives
Troubleshooting
Timeout Issues
Timeout Issues
If analysis times out frequently:
- Increase timeout with
--malware-analysis-timeout - Scan smaller package sets
- Check network connectivity to SafeDep Cloud
Authentication Problems
Authentication Problems
If malware analysis fails with auth errors:
- Verify API key has malware analysis permissions
- Check tenant configuration
- Ensure you’re using vet v1.9.7 or later
False Positives
False Positives
If legitimate packages are flagged:
- Review the analysis details
- Contact SafeDep support with package details
- Use exceptions management for temporary overrides

