vet supports exporting policy violation reports as SARIF which can be uploaded to GitHub.
Quick Setup with GitHub Action
vet has a dedicated GitHub Action for easy integration. This is the recommended approach for most teams.
Basic Configuration
Create.github/workflows/vet.yml in your repository:
SARIF reports work when you enable GitHub Code Scanning in your repository. Learn more
Advanced Configuration
For more control over the scanning process:Manual SARIF Generation
You can also generate SARIF reports manually using thevet CLI:
Viewing Results
Once the SARIF report is uploaded to GitHub, policy violations will be available in the GitHub Security tab. This provides a centralized view of policy violations across different repositories.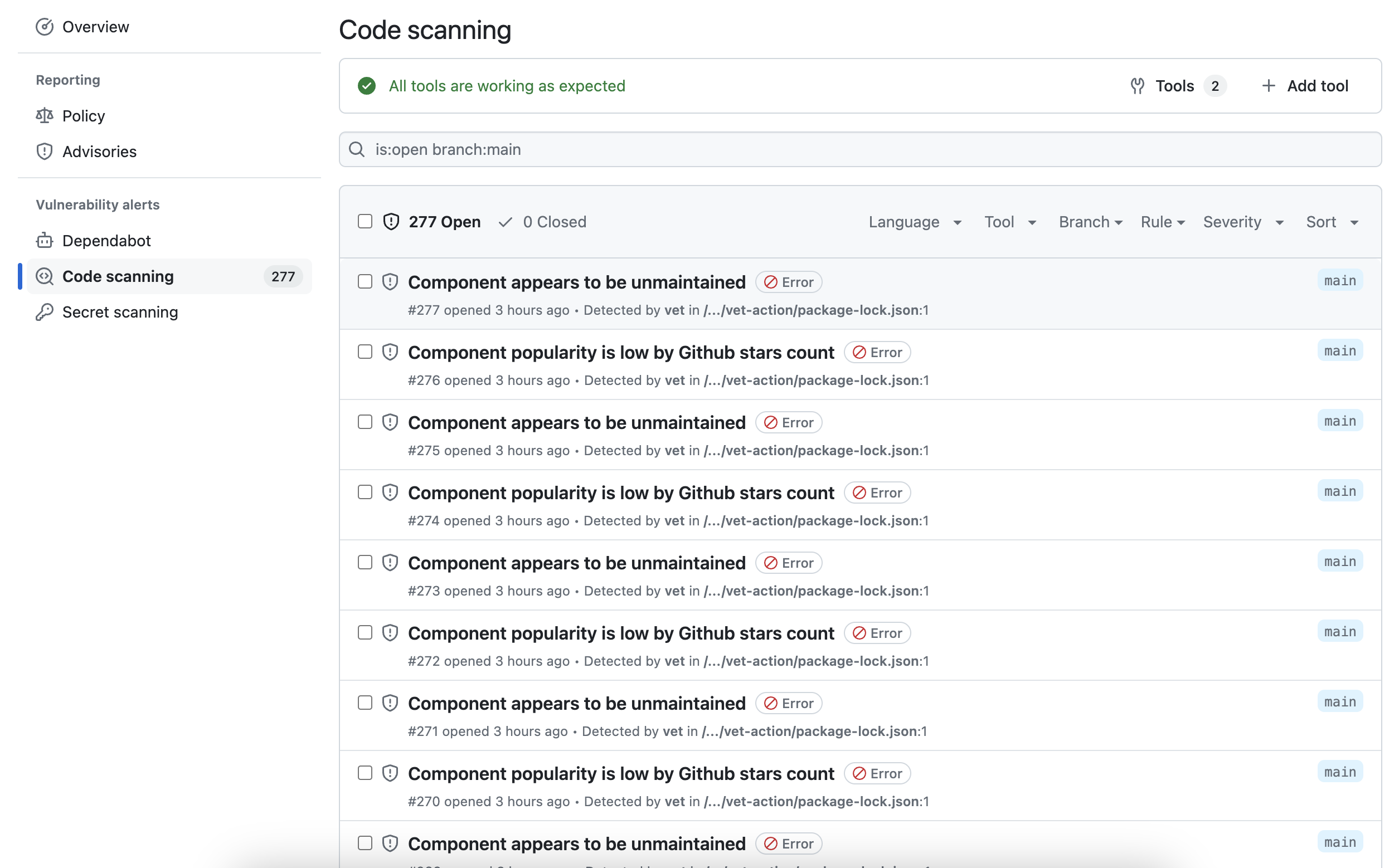
Pull Request Integration
The GitHub Action automatically adds comments to pull requests when security issues are found: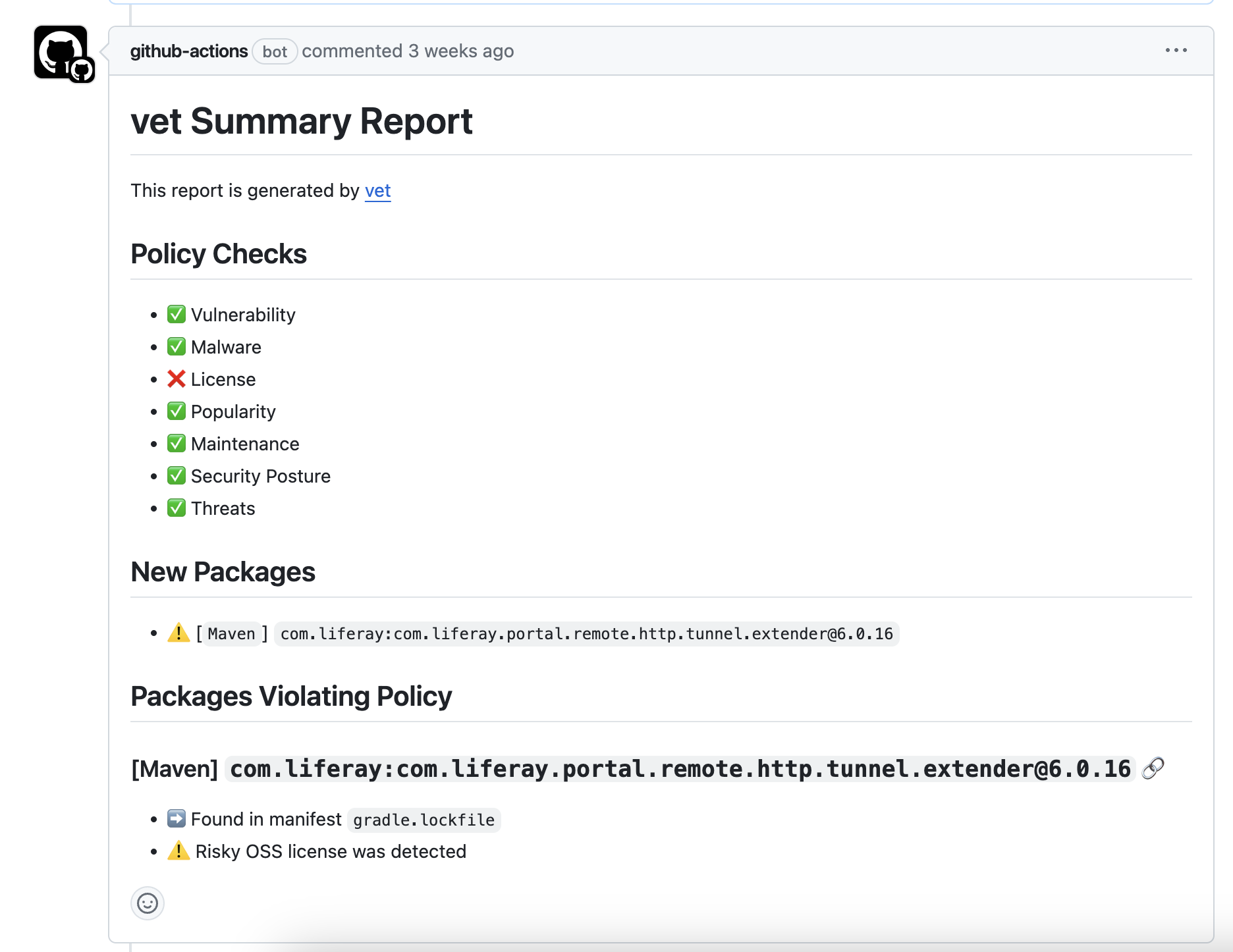
Best Practices
Policy Configuration
Policy Configuration
Store your vet policies in version control (e.g.,
.github/vet/policy.yml) to ensure consistent security standards across your organization.Branch Protection
Branch Protection
Configure branch protection rules to require the vet check to pass before merging pull requests.
Organization-wide Deployment
Organization-wide Deployment
Use GitHub organization templates to deploy vet across all repositories automatically.
Troubleshooting
SARIF Upload Fails
SARIF Upload Fails
Ensure the
security-events: write permission is set in your workflow file and that Code Scanning is enabled for your repository.No Violations Reported
No Violations Reported
Check that your policy configuration is correct and that violations actually exist. Use
--report-json locally to debug.
